binary from pwnable.tw Spirited Away
# 0x00 Abstract
Easy house of spirit.
# 0x01 Function analysis
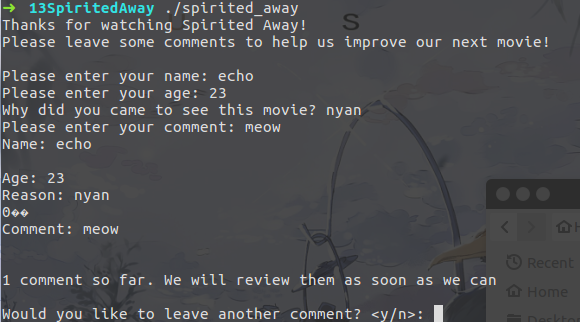
Play with this binary. Finding it only provide commenting function. It require you to input your name, age, reason, comment.
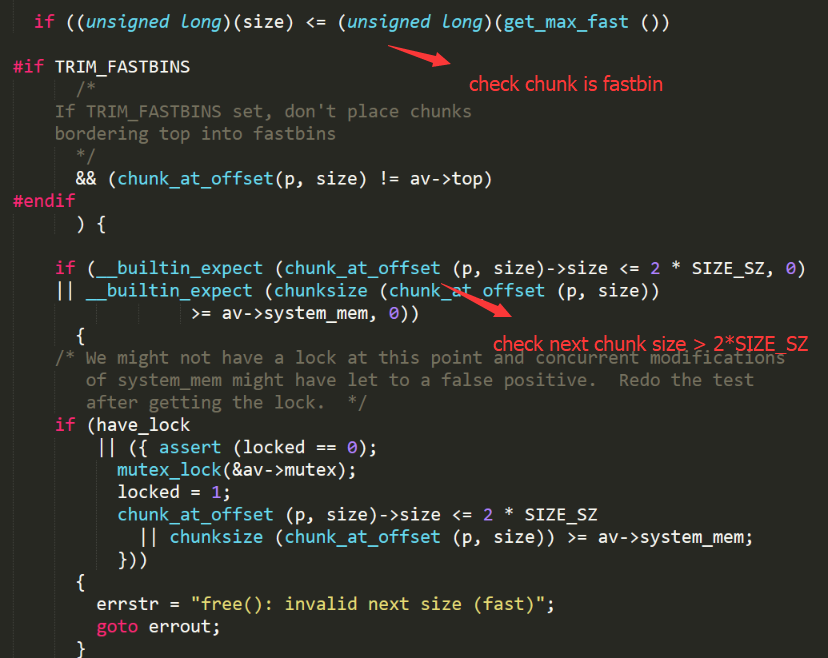
Reverse this binary, We can figure out the vulnerabilities
- When cnt larger than 99, the length of s is 57. So the name_comment_len will be covered with ascii ‘n’ (hex in 0x6e).
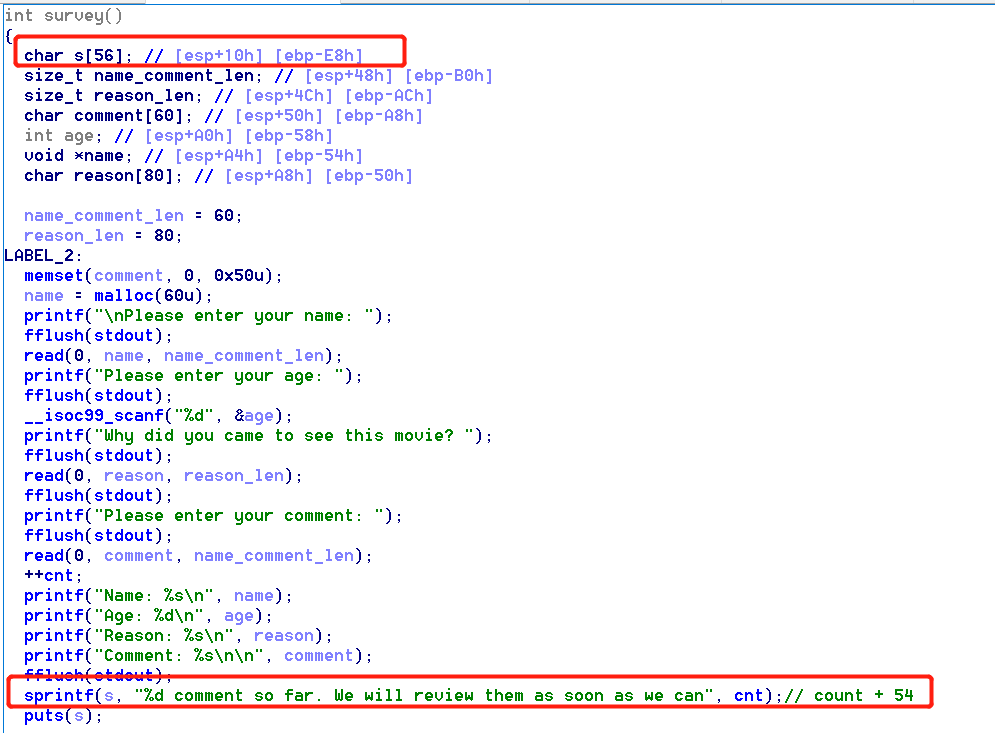
- After we control name_comment_len, we can fill comment with 0x6e length. So we can control the name pointer to where we want. If you make it point to stack and make a fake heap struct, next time you malloc, you will get a heap struct in stack.
pwnable.tw said “Do not share the solutions of high score challenges in public”. So I will not offer the exp.
# 0x02 Make fake heap
The most important of this challenge is to make fake heap struct. In this place, I will give a graphic to show what the heap struct really is. First is the heap struct in use.
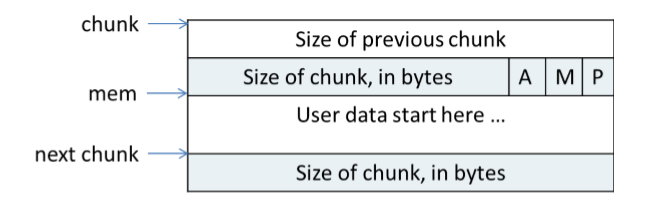
Next is the heap struct not in use.
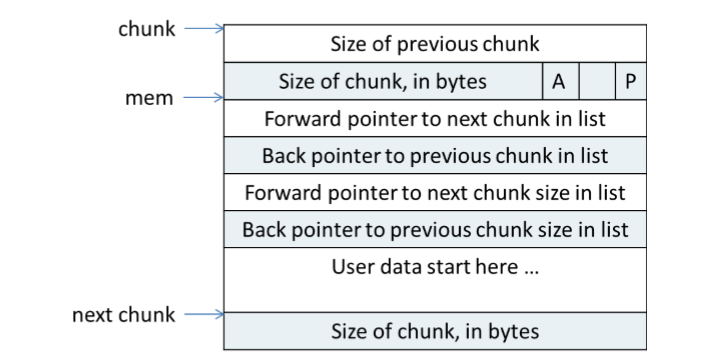
Here I will not explain what the every variable means. If you have problem with it, just google.
But make a fake heap struct is not enough. We need to make two fake heap struct. This is because free function require next chunk size larger than 2*SIZE_SZ (SIZE_SZ = 4 in x86 system). But the size is not size>>3*8. It contains flag bits. So if you set it 9 or 0xa, it is okay.