binary from pwnable.tw Secrect garden
# 0x00 Abstract
When a chunk is first unsorted bin chunk, its bk&fd pointe to main_arena+88, either you leak it by using output, or use unsorted bin attack to set an address to main_arena+88.
# 0x01 What is unsorted bin
System using unsorted bin to give the recently released chunk a second chance of malloc. Use unsorted bin can accelerate system allocation of memory. Because the entire operation no longer takes extra time to find the right bin.
Unsorted bin manages chunks using a circular double-linked list. In the process of using, the traversal order used is FIFO.
Unsorted bin is stored in the first unit of Bins in main_arena.
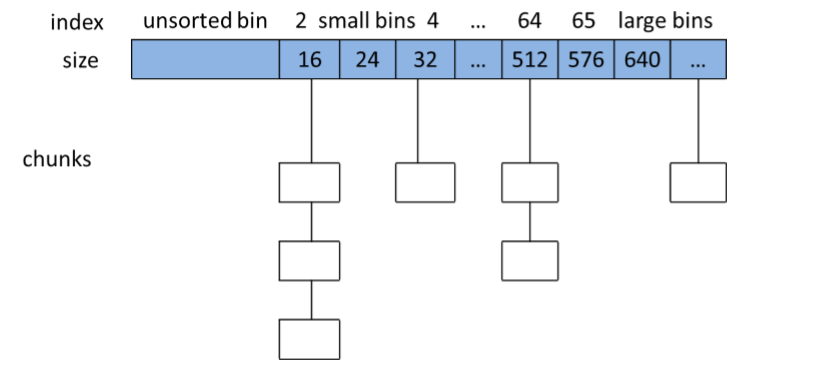
There are usually three ways to put a chunk into the unsorted bin list.
- 1 When a large chunk is split into two halves, if the rest is greater than MINSIZE, it will be placed in the unsorted bin.
- 2 When a chunk that does not belong to the fast bin is released, and the chunk is not adjacent to the top chunk, the chunk is first placed in the unsorted bin.
- 3 When malloc_consolidate is executed, the merged chunk may be placed in the unsorted bin if it is not near the top chunk.
# 0x02 How to leak libc base address
As mentioned above, unsorted bin is stored in the first unit of Bins in main_arena. And main_arena is stored in memory as a global variable.
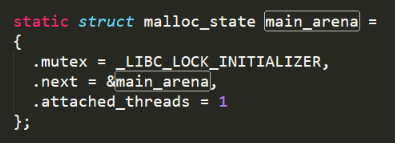
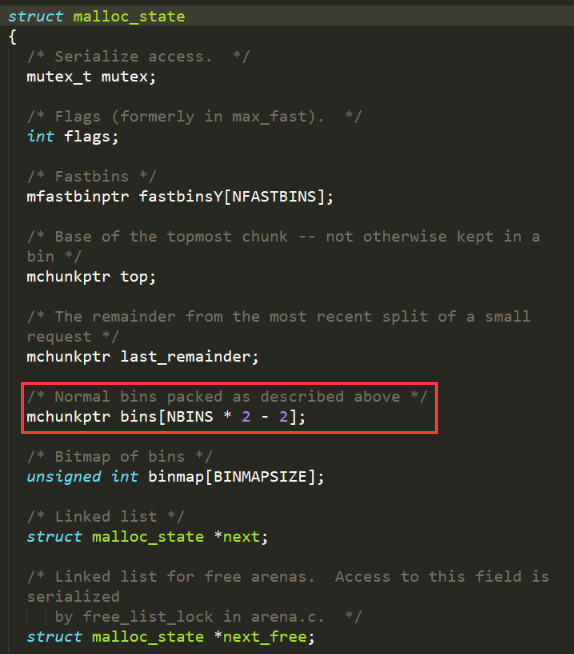
If a chunk was recently placed in unsorted bin, then its bk pointer points to the first unit in the main_arena Bins.
The difference between this address and the libc base address is fixed. If we can leak this address, we can calculate the base address of libc based on the difference. It should be noted that the difference will vary depending on the libc.
# 0x03 Unsorted bin attack
The reason of unsorted bin attack is from the libc source code
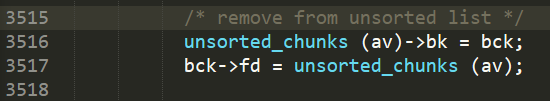
If you can control bk of unsorted bin, next time you malloc it, it will change the bck->fd to main_arena+88.
Unsorted bin attack need support of uaf vulnerability.
Unsorted bin attack as following:
- 1.Malloc a big chunk and free it to get unsorted bin.
- 2.Use uaf vulnerability to make its bk point to where you want.
- 3.Malloc the same size chunk to trigger this attack.